How to Grant User Api Access to Gsuite
To improve security, an administrator can block all third-party API app access to Workspace data, but more targeted methods may be better overall.

Recently, Google added a Workspace security setting that lets an administrator choose to block all third-party API access. By default, the setting is not active, but when enabled, it blocks OAuth and API connections between your organization's Google Workspace accounts and third-party apps. Apps added by an administrator from the Google Workspace Marketplace retain access and continue to have trusted access.
After the feature was announced, I noticed at least one Google Workspace consultant encouraging administrators to enable the feature. On Twitter, they recommended that Google Workspace administrators who are concerned about security turn the feature on immediately to prevent people from signing in to third-party apps and websites with their Google Workspace account.
From a strict security perspective, it does seem logical that restricting access protects organizational data. Sign in to the Google Admin console, select Security | API Controls and enable the check box next to Block All Third-Party API Access. Select Save and you're done. Third-party apps can't get at your Workspace data. That's obviously more secure than letting third-party apps access your Workspace data. Right? Maybe not.
SEE: Shadow IT policy (TechRepublic Premium)
This sort of lockdown ignores how people behave. In my experience, when people can't sign in to an app with an organizational account, they often sign in to third-party apps with a personal account. That action makes third-party app access harder to detect and monitor, not easier. Is that better? I don't think so.
Instead of blocking third-party API access for your organization's domain entirely, I suggest Google Workspace administrators take the following four steps to monitor sign-ins, communicate with people about app needs and security and then adjust access to each specific app, as appropriate.
How to review current third-party app access
On the same page as the option to block all third-party API access, Google gives administrators access to a Manage Third-Party App Access link (Figure A).
Figure A

In the Security | API Controls section of the Google Admin console, an administrator can Block All Third-Party API Access. However, most administrators will want to Manage Third-Party App Access and adjust access for individual apps, instead.
This provides a Workspace administrator the list of apps with access to Google Workspace data. The list can display the application name, number of users, verified status, requested services, as well as the extent of access (e.g., trusted, limited or blocked).
The app access information allows an administrator to identify tools already accessed by some people in the organization (Figure B).
Figure B

A Google Workspace administrator may review all third-party apps with API access connected to the organization's accounts.
In some cases, an administrator might use this information to encourage additional adoption. For example, if you know that many people use an app such as Todoist or Asana, it can make it easier to encourage others to do so, also. This list also has the potential to help save money, since individual subscriptions tend to cost more on a per account basis than organizational subscriptions. Widely-used apps may merit a switch from individual to enterprise subscription management.
(Optional) How to review individual third-party app access
If a Workspace administrator has specific concerns about app access by a particular person, the administrator may review individual sign-ins to third-party apps. Sign in to the Google Admin console, go to the list of users, then follow the link on the individual's name to access account details. In the Security section, look for the list of Connected Applications (Figure C).
Figure C

A Google Workspace administrator also may review third-party applications connected to each user's account in the organization.
Be sure to communicate before you make changes
I encourage administrators to communicate to people in the organization prior to any changes. Let people know which app (or apps) presents any cause for concern, indicate your potential course of action (e.g., upgrade to paid enterprise accounts, limit or block access) and ask for comments. A willingness to engage in a dialogue and talk about potential security concerns, subscriptions or cost savings creates a much more productive work environment than one where an administrator simply shuts down access without engagement or explanation.
How to adjust specific third-party app access to Workspace data
Instead of a complete block on all third-party API access, you may modify access for individual apps. Place your cursor over an app on the list, then select Change Access.
You may select from three options, as shown in Figure D: Trusted (to allow the API to access all Google services), Limited (to allow access only to unrestricted Google services) or Blocked (to prevent all API access). An adjustment to Trusted should be rare. Instead, most apps should be set to Limited.
Figure D
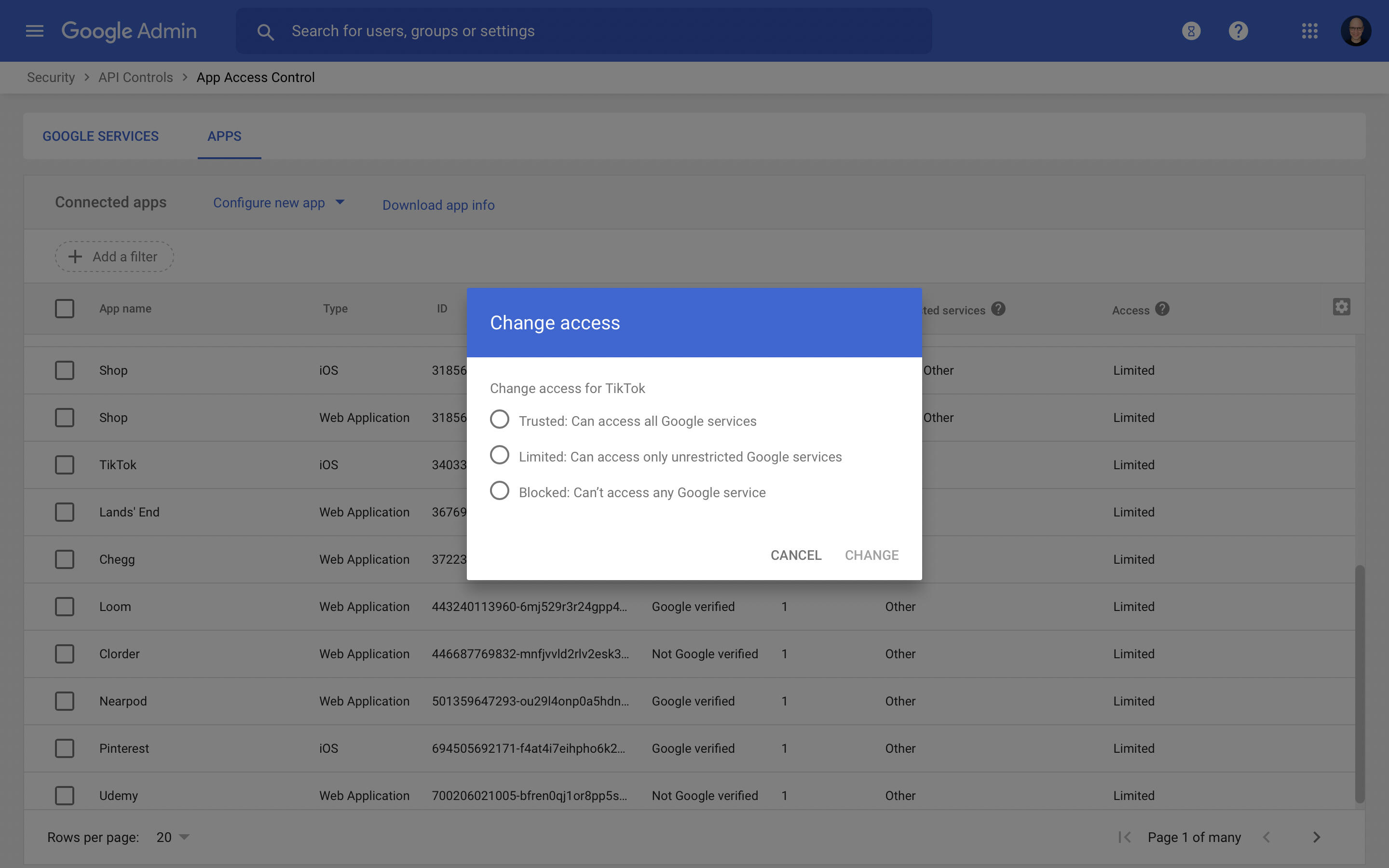
When adjusting third-party app access settings, an Administrator may choose from Trusted, Limited or Blocked.
A decision to Block a service should be done cautiously. For example, an administrator might certainly have reasonable concerns about allowing organizational accounts to access TikTok. However, some people in the organization (maybe a marketing and social media promotions team) may be using the app to engage potential customers. Similarly, access to retail sites, such as Lands' End, for example, might have a reasonable corporate use, such as the purchase of clothing for team members. A block means people might create accounts with addresses outside of the organization's control. Which presents a bigger risk—visibility that an app is in use, but with limited access, or a block that pushes people to personal account usage?
What approach do you support?
I view Google's new setting as an additional tool for administrators to use in the ongoing attempt to balance concerns of system administrators about security and daily desires of people who want to use apps and services. In a few high-security organizations—healthcare, government or financial services—a complete block of all third-party API access may make sense.
People in those organizations (hopefully) already operate with a relatively strong understanding of the need for security and privacy of data. In most organizations though, a less stringent prudent practice would be to regularly review third-party API access. After each review, engage with people about any potential changes or restrictions, if needed.
If you use Google Workspace, what approach to connected app and/or third-party API access does your organization take? If you're an administrator, have you chosen to block all third-party API access or not? Why? How well do administrators in your organization communicate concerns or engage with account holders? Let me know what your experience has been, either in the comments below or on Twitter (@awolber).

Google Weekly Newsletter
Learn how to get the most out of Google Docs, Google Cloud Platform, Google Apps, Chrome OS, and all the other Google products used in business environments. Delivered Fridays
Sign up todayAlso see
- Top cloud providers in 2020: AWS, Microsoft Azure, and Google Cloud, hybrid, SaaS players (TechRepublic Premium)
- New survey details IT challenges, shadow IT risks, 2021 outlook, and more (TechRepublic)
- Shadow IT: The challenges and opportunities (TechRepublic)
- Google Workspace admins: How to review your data protection insights report (TechRepublic)
- Google takes stance against permission-grabbing Chrome extensions (ZDNet)
- How-To Tips: More easy-to-follow tutorials (TechRepublic on Flipboard)
How to Grant User Api Access to Gsuite
Source: https://www.techrepublic.com/article/how-to-manage-third-party-app-api-access-in-google-workspace/
0 Response to "How to Grant User Api Access to Gsuite"
Post a Comment